

Operational Technology (OT) and IT are growing together. They have to in order to be competitive! The objective: to use data profitably. According to different studies, the majority of companies in Germany see a high level of digitalization in 
The convergence of OT and IT increases the attack surface and puts production machines in the crosshairs of attackers. This report discusses how professional cyber security is applied in Industrial Digital Transformation. At the same time, the limits of the known cybersecurity methods are shown. It is time for end users to rethink their cybersecurity strategies and start looking at new ways to protect their human and physical assets. Cyber immunity is a new concept where Cyber-immune systems have to innate ability to withstand whole classes of cyberattacks, including new infectious agents that are invisible to classic cybersecurity solutions.
Industry 4.0 and the industrial internet of things (IIoT) have numerous aspects, and there is not always agreement on what exactly is meant by these terms. Before we define what Industry 4.0 or IIoT exactly is, we should first explain what the digital transformation can achieve. The use of digital technologies in industry will bring about a multitude of new production processes, business models, and products. A product line, for example, no longer must be fixed to one product. This will change the requirements for industrial manufacturing. IT support will make it possible to flexibly adapt processing stations to a changing product mix. In the process, capacities can be optimally utilized. In addition, the 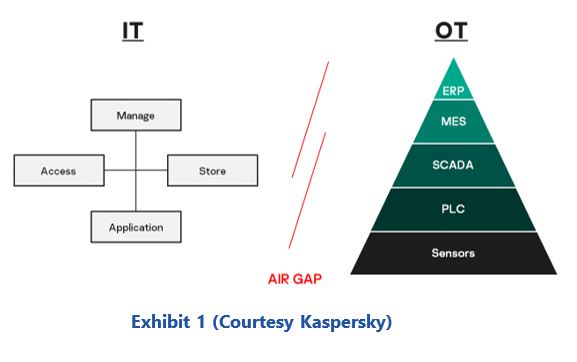
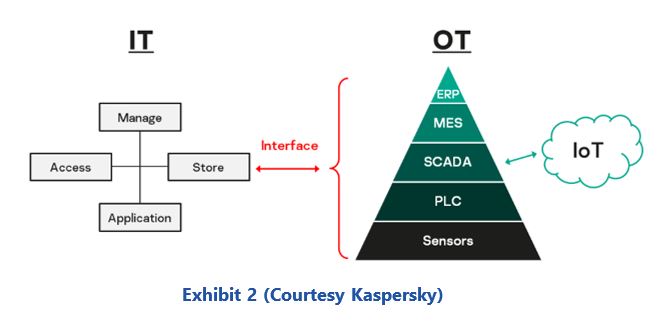
That is why the strict separation between IT and OT has not existed for a long time. This separation has been eliminated in many places, and not just in the context of the digital transformation. Machines have had remote maintenance access for a long time, via which the manufacturer carries out remote maintenance. Remote maintenance is the best way to implement short response times to problems in a cost-effective and timely manner.
Consequently, this means that there will not be several separate IT worlds, but only one. The question of IT security remains. Are the "usual" mechanisms used in IT and OT sufficient to realize the required security standard in this world of convergence of production and office IT? Is the usual level of IT security sufficient at all when production facilities are digitally upgraded and networked? If not, what level is required?
Industry is already exposed to an elevated risk from cyber threats. Digital transformation will certainly create more vulnerabilities in the OT infrastructure in the medium term. Therefore, cybersecurity must be rethought so that in the future, the increase in efficiency due to digital transformation is not destroyed by cyber threats.
A fundamental approach to IT security is standardization and updating and hiding of information regards the security measures. In office IT, this standardization is achieved, among other things, by regularly and comprehensively installing security updates to close security gaps. It is precisely at this point that OT differs from IT. After the successful initial commissioning of a plant, the software, e.g., operating system and control programs, are frozen, "never touch a running system".
There are even more highly specialized OT security tools available. On the one hand, brownfield assets (existing assets) need to be protected. For this, Kaspersky offers tailored solutions such as KICS for networks or endpoints. For flexible requirements in new OT infrastructures like IIoT, Kaspersky has developed the Cyber Immune concept.
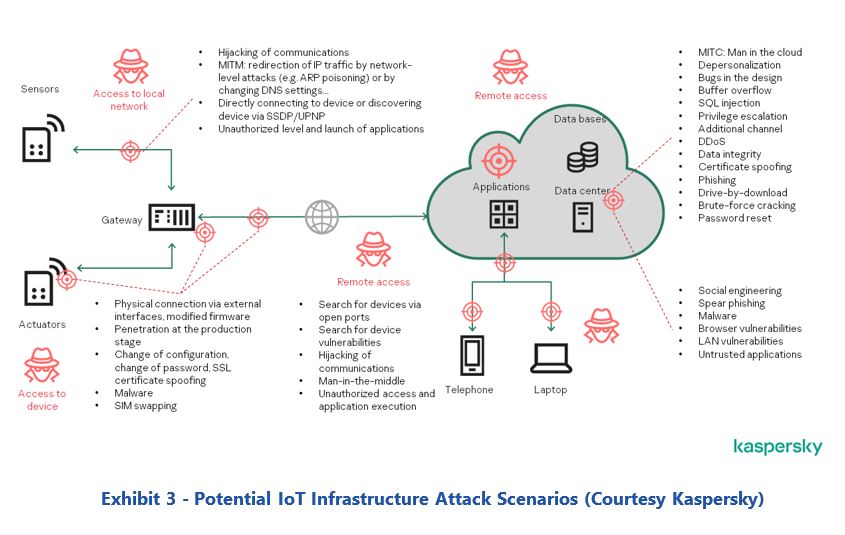
But due to the growing number of IIoT components in the production environment, these communication structures are becoming increasingly complex, and it seems hopeless to introduce a meaningful zoning in these growing communication structures. Two other facts that affect IIoT systems are that most components cannot be easily patched, and the software is poorly protected against manipulation. In this situation, new, simple strategies are needed to ensure IT security over the long lifecycle of the production equipment.
Today there are millions of control systems and billions of IIoT components operational, and these are growing every day. That means the industry invests and maintains a growing number of cybersecurity appliances to protect the control infrastructure. Does this investment and the level of protection it provides really make sense? Or is it better to completely rethink the cybersecurity strategy and proactively address the new requirements of control equipment in the era of IIoT?
Kaspersky has seen the changing needs of its clients and wider market through their digital transformation journey. Industrial Cybersecurity is a major focus of the organization. Alongside their current OT security products, Kaspersky and its partners announced the first industrial gateway with a “secure by design” architecture at the Hanover Fair in 2019.
We will first look at the operating systems currently in use. These were developed in principle in the 1970s. These systems contain different layers. First there is the base layer, which controls the hardware-related functions. This is followed by the application layer, where the software runs. At the very top is the security layer, where unauthorized access is rejected, but if the security layer is breached, the attacker has access to the subordinate layers and can manipulate functions there. Cyber Immune components are built differently. The architecture is based on a microkernel structure.
True to their name, microkernels are quite small in size. With respect to software, this means that their functions and architecture can be understood by a human without the need for a technical manual.
Microkernels provide a minimal set of basic process management functions and hardware abstractions. Most of the remaining hardware and software support is done through special processes that run outside of the kernel address space. This allows the attack surface to be reduced significantly. In addition, the smaller the codebase of the OS kernel, the easier it is to monitor and check for errors, both manually and automatically. But it is not enough to provide an optimal amount of code for each software module. The interfaces between modules also need to remain low complexity.
The core function "Cyber Immune" means that an IIoT device can be networked with other automation devices without additional security functions. This is a significant simplification for the user. If more IIoT components are used in the future, then the Cyber Immunity concept will simplify the lifecycle maintenance of these components.
Digitization combines information technology (IT), traditional operational technology (OT) and intellectual property (IP) together to boost industry competitiveness.
That is why this merging of OT, IT and IP can be observed in the manufacturing industry. To fully realize this networking is a task that takes some time for most companies. Thus, we can observe how an entire industry is slowly moving towards Industry 4.0 by replacing equipment piece by piece. Unfortunately, this transformation brings a number of new cyber-threats and -risks.
Overall, IT security must become a matter of course - and not in the sense of running in parallel, but rather being thought of from the very beginning. ICS Systems have lifetimes of more than 30 years. New cyber security concepts such as Cyber Immunity are needed here. A system that protects against current and future cyber threats is certainly a very practical method. Cyber Immunity can be the new foundation how the digital transformation will be implemented more securely.
ARC Advisory Group clients can view the complete report at ARC Client Portal
If you would like to buy this report or obtain information about how to become a client, please Contact Us
Keywords: Kaspersky, Cyber Immunity, KasperskyOS, ARC Advisory Group.

