

The market for OT level cybersecurity services is growing rapidly. End users simply do not have the internal resources required to perform all the tasks necessary to develop and maintain an effective and resilient cybersecurity posture. Myriad suppliers offer OT level cybersecurity services, from traditional automation suppliers to systems integration firms, engineering and design firms – even traditional IT level suppliers are offering these services.

The range of services for OT cybersecurity today can be grouped into three primary areas: assessment services, design and implementation services, and managed services, and end user requirements will vary among these three categories. Knowledge of OT systems is important whenever you make a contract for cybersecurity services. Ideal partners have expertise in your industry, are familiar with your ecosystem of equipment and applications, and have strong connections with your automation OEMs. Industries vary in the security regulations and standards they need to satisfy, so any potential partner will have to be well-versed in whatever standards, frameworks, or regulations are relevant to you.
Digital transformation and the rise of cyber physical systems also complicate the search for an effective service provider. The increasingly large installed base of what would traditionally be called IT assets at the OT level, including industrial edge computing platforms, cloud computing environments, and industrial IoT data platforms, must also be considered. Having knowledge of proprietary automation systems and equipment is no longer enough. Any good OT level cybersecurity service provider should be able to bridge the gap between IT and OT and provide a more holistic view of security.
ARC recently discussed these issues and more with global OT cybersecurity service provider L&T Technology Services (LTTS). As an engineering leader, LTTS can leverage its deep expertise in a wide range of industry segments and applications to provide a full scope of cybersecurity services from assessments to engineering, design, and deployment of cybersecurity solutions, as well as managed security services.
Not surprisingly, this market for security services has a very broad mix of suppliers. These include automation suppliers, control system integrators, niche ICS cybersecurity service companies, and IT/OT cybersecurity service providers. Some focus exclusively on assessments, while others see this as the entry point for larger contracts. Selecting the right supplier for OT/ICS cybersecurity can be a challenge. End users should develop selection criteria based on both business and security requirements. Cost is only one dimension of selection, and it’s not the most important. How much industry expertise does your potential partner have? What about regional strengths or ability to provide end-to-end solutions? Let’s examine some key selection criteria.


Knowledge of OT systems is important whenever you make a contract for cybersecurity services. Ideal partners have expertise in your industry and with the specific equipment you use. Industries vary in the security regulations they need to satisfy. OT equipment suppliers vary in the protocols and security products they use. Cybersecurity service providers may also need support from automation suppliers in diagnosing and resolving problems. Established relationships can be incredibly helpful in ensuring that this support is provided in a timely manner.
Cybersecurity service providers vary in their capabilities and focus. Security operations center (SOC) support may be vital in the event of a cyber incident, but a company focused on this issue may not have the local resources that are needed to support your vulnerability management needs. The best situation is when a single supplier can satisfy all your needs. This will reduce cybersecurity management issues and facilitate efficiency. It also reduces the need to coordinate services across various service providers.
Service provider contracts should be viewed as long-term partnerships. The high costs of changing service providers and the potential risks of service lapses can be high. Ideally your service provider can help you plan, implement, and maintain the changes that will be needed to secure new developments like digital transformation, cloud migration, and connected workers.
While the business driven world of IT and the production and operations driven world of OT still have different operational requirements, they can no longer be viewed as separate. More IT focused cybersecurity practices are finding their way into the OT world as industrial control systems increasingly incorporate cloud computing, edge processing, virtualization, and industrial IoT-specific protocols. From a cybersecurity, incident prevention, and mitigation perspective, the IT and OT domains are closely intertwined. A loss of visibility at the IT level frequently results in an unexpected shutdown at the OT level, as we saw with the Colonial Pipeline incident for example. For industrial end users, a depth of expertise in OT as well as IT cybersecurity can be a significant advantage for a cybersecurity service provider.
A subsidiary of one of India’s largest engineering conglomerates Larsen & Toubro, L&T Technology Services (LTTS) is a leading global services company with a client base comprising 69 Fortune 500 companies and 53 of the world’s top R&D spenders. The consultancy, design, development and testing services across the product and process development lifecycle cater to all major industries including transportation, industrial products, telecom & hi-tech, medical devices, and the process industries. LTTS specializes in an array of advanced technologies, including 5G, artificial intelligence, collaborative robots, digital factories, autonomous vehicles, and more.
With more than two decades of experience providing industrial automation and cybersecurity solutions, LTTS offers a wide range of industrial cybersecurity services to help clients secure their operational technology (OT) environments. LTTS’ portfolio of services covers the entire lifecycle of OT security, from design and implementation to SOC design and managed security services. LTTS leverages its deep domain and engineering knowledge, strong partnerships, and experience in deployment of new technologies to deliver solutions that meet the specific needs and challenges of different applications, from the heavy process industries to discrete manufacturing and critical infrastructure.
As a leading engineering firm for the process industries and other sectors, LTTS brings a wealth of engineering, process, and application knowledge to the world of industrial cybersecurity services. LTTS also has a wide breadth of industry specific engineering knowledge that includes not only process, hybrid, medical, transport, and discrete manufacturing applications, but also product design, application development, penetration testing, and other product and application related services.
LTTS offers a full range of industrial/OT cybersecurity assessment services, including consulting and advisory services, asset identification, profiling, and inventory, development of security roadmaps, assessment and mitigation reporting, network architecture review, and vulnerability identification and reporting. LTTS assessments are performed to conform to generally accepted guidelines and standards. This includes the NIST Cybersecurity Framework, ISA99/IEC-62443, NERC-CIP, ENISA, NESA, OTCC and NIST 800-82. In some cases, users may also expect assessments to include compliance with specific industry standards and practices.
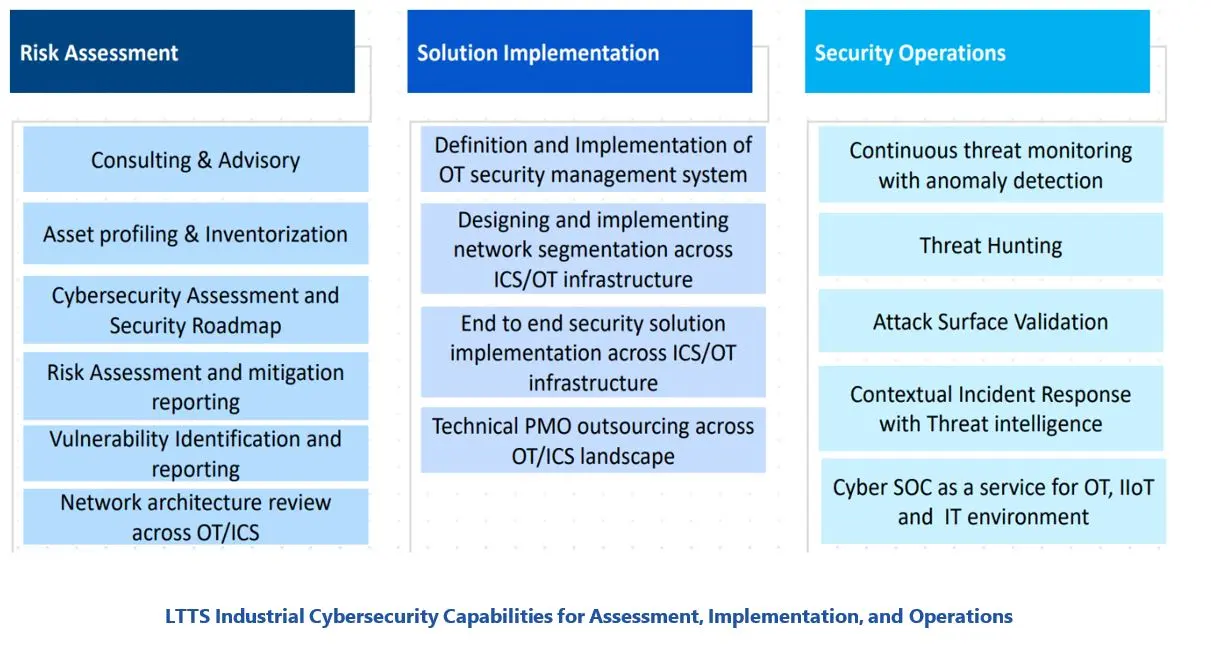
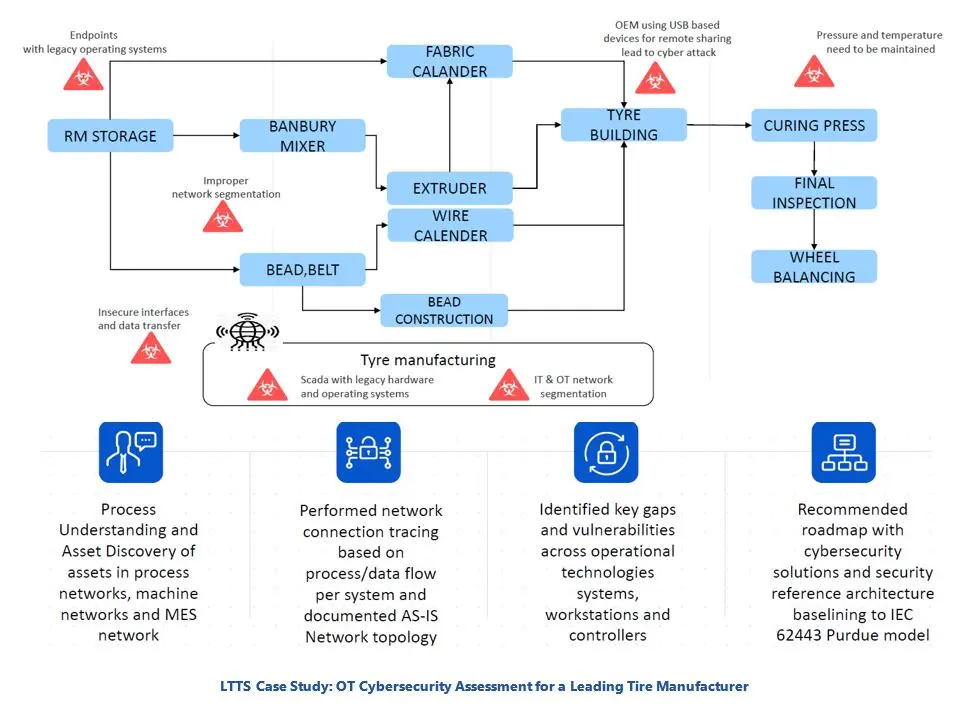
Industrial/OT cybersecurity design services focus on ensuring that new facilities or upgrades to existing facilities are built with security in mind. This includes developing security architectures and policies, selecting and configuring security devices and software, integrating security features into control systems and networks, and testing and validating security functionality. LTTS can help clients design resilient OT security systems that comply with relevant standards and best practices, such as ISA99/IEC-62443, NIST 800-82, and ISO 27001. LTTS can also provide guidance on how to incorporate security into the project management and engineering processes, as well as how to train and educate staff on security awareness and skills.
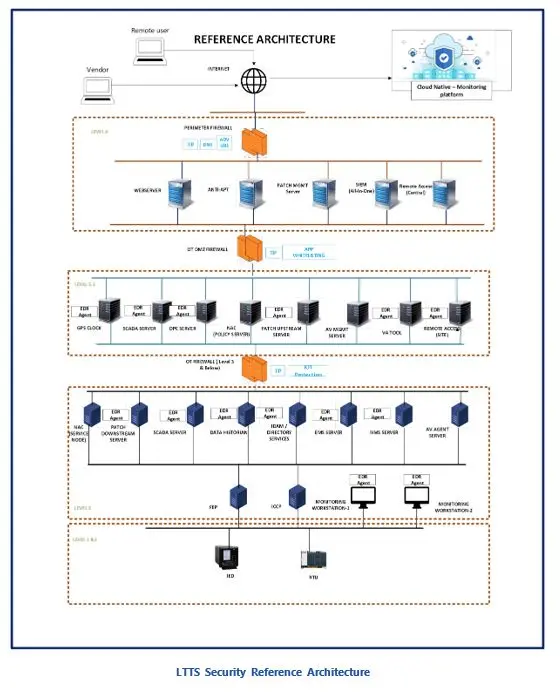
OT cybersecurity implementation services involve deploying and activating security solutions in the operational environment. This includes installing and configuring security hardware and software, setting up firewalls and VPNs, implementing encryption and authentication mechanisms, applying patches and updates, and performing penetration testing and vulnerability scanning. LTTS can help clients implement OT security solutions with minimal disruption to production and operations, while ensuring that the solutions are properly integrated with the existing infrastructure and systems. LTTS can also provide support for troubleshooting and resolving any issues that may arise during or after the implementation phase.
Industrial/OT cybersecurity monitoring services focus on detecting and responding to security incidents and threats in the operational environment. This includes collecting and analyzing security data from various sources, such as logs, alarms, alerts, and events, identifying and prioritizing potential risks and attacks, and initiating and executing appropriate countermeasures and remediation actions. LTTS can help clients monitor their OT security systems using advanced tools and techniques, such as anomaly detection, machine learning, artificial intelligence, and threat intelligence. LTTS can also provide real-time visibility and reporting on the security status and performance of the OT systems, as well as recommendations for continuous improvement and optimization.
In addition to monitoring services, LTTS can also offer end-to-end managed security services for the industrial/OT environment, including managed security operations center (SOC) capabilities. This includes designing, implementing, maintaining, and updating the security infrastructure, policies, and procedures, as well as providing ongoing support and guidance on best practices and compliance requirements.
LTTS has a strong partner ecosystem that includes a wide range of both OT/industrial cybersecurity suppliers and control system and automation suppliers. Major DCS supplier partners include ABB, Emerson, Honeywell, Rockwell Automation, and Siemens. The company has several other relationships with OT level suppliers for a wide range of systems and applications, including Schneider Electric, Beckhoff, Yokogawa, GE, Mitsubishi, Omron, AVEVA, and more. OT cybersecurity partnerships include Palo Alto Networks, Claroty, and more.
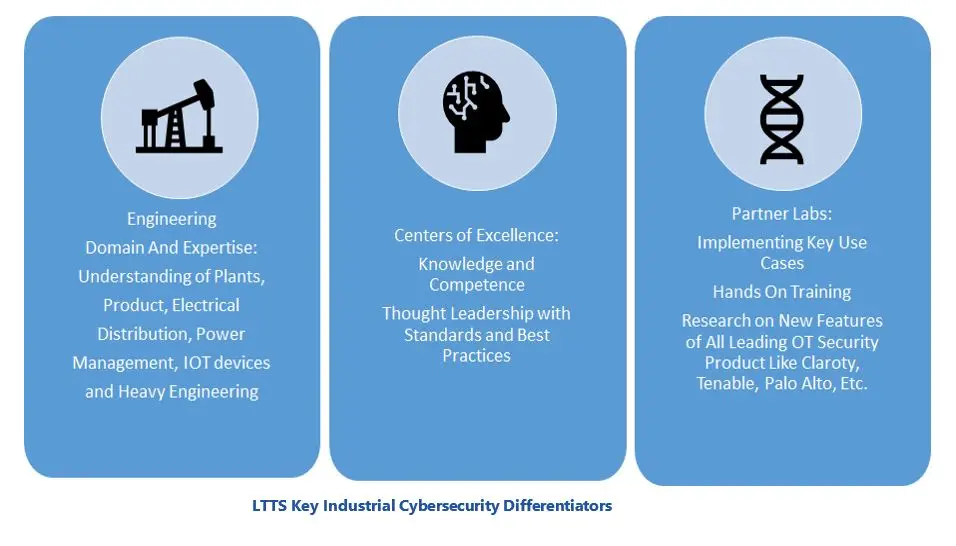
Cybersecurity service providers come in all shapes and sizes, and from different businesses, from automation suppliers to standalone service providers, engineering firms, systems integrators, and more. End users must evaluate potential service providers based on their own requirements and standards. LTTS provides a wide range of industrial/OT cybersecurity services that benefit from the company’s deep engineering and domain expertise. In addition to understanding plants and how they are designed, LTTS understands the electrical domain, rapidly emerging technologies like 5G and IoT devices and platforms, and heavy engineering. LTTS also has a strong partner ecosystem and deep knowledge in control system and automation design and engineering.
ARC Advisory Group clients can view the complete report at the ARC Client Portal.
Please Contact Us if you would like to speak with the author.
You can learn more about cybersecurity at Industrial Cybersecurity Market Analysis Research

